It's starting to look like Superfish and other software containing the same HTTPS-breaking code library may have posed more than a merely theoretical danger to Internet users. For the first time, researchers have uncovered evidence suggesting the critical weakness may have been exploited against real people visiting real sites, including Gmail, Amazon, eBay, Twitter, and Gpg4Win.org, to name just a few.
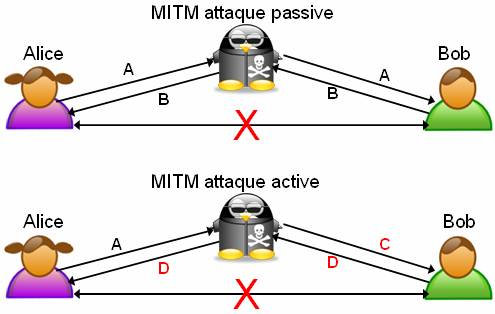
As Ars reported one week ago, ad-injecting software pre-installed on some Lenovo laptops caused most browsers to trust fraudulent secure sockets layer certificates. The software was called Superfish. In the coming days, security researchers unearthed more than a dozen other apps that posed the same threat. The common thread among all the titles was a code library provided by an Israel-based company called Komodia.The Komodia library modified a PC's network stack by adding a new root Certificate Authority certificate. Poor choices in both the way the certificate and underlying code were designed caused most browsers to trust fraudulent certificates that otherwise would have generated warnings. Flagrantly fraudulent certificates got a pass as long as they (a) contained the same easily extracted private key baked into the app or (b) contained the name of the targeted website in certificate's alternate name field. Malicious hackers could exploit this failure to masquerade as secure pages for Bank of America, Google, or any other website on the Internet. As a result, attackers had an easy way to wage man-in-the-middle attacks against otherwise secure HTTPS connections.
Until now, that danger was nothing more than a troubling hypothetical, but no more. On Wednesday, researchers presented evidence attackers have exploited the weaknesses in Superfish and the other programs to launch real man-in-the-middle attacks on end users as they visited some of the most sensitive HTTPS-protected websites on the Internet. In a blog post published Wednesday, Researchers Joseph Bonneau and Jeremy Gillula wrote:
We searched the Decentralized SSL Observatory for examples of certificates that Komodia should have rejected, but which it ended up causing browsers to accept, and found over 1600 entries. Affected domains included sensitive websites like Google (including mail.google.com, accounts.google.com, and checkout.google.com), Yahoo (including login.yahoo.com), Bing, Windows Live Mail, Amazon, eBay (including checkout.payments.ebay.com), Twitter, Netflix, Mozilla’s Add-Ons website, www.gpg4win.org, several banking websites (including mint.com and domains from HSBC and Wells Fargo), several insurance websites, the Decentralized SSL Observatory itself, and even superfish.com.
While it’s likely that some of these domains had legitimately invalid certificates (due to configuration errors or other routine issues), it seems unlikely that all of them did. Thus it’s possible that Komodia’s software enabled real MitM attacks which gave attackers access to people’s email, search histories, social media accounts, e-commerce accounts, bank accounts, and even the ability to install malicious software that could permanently compromise a user’s browser or read their encryption keys.
The researchers went on to note that one or more versions of Privdog—an application created and marketed by the same people behind the Comodo certificate authority that produces more than a third of the Internet's SSL certificates—had an even more severe defect than the Komodia-derived software. It caused browsers to accept any fraudulent certificate no matter what private key it used or what was contained in the alternate name field.
"The Decentralized SSL Observatory has collected over 17,000 different certificates from PrivDog users, any one of which could be from an attack," the EFF researchers wrote. "Unfortunately, there’s no way to know for sure."
The past seven days have been unsettling. It's hard to understand how vulnerabilities this serious went undetected for so long, and it's disappointing that Superfish's CEO has yet to acknowledge his company's role in this security debacle. The revelations aren't getting any easier to digest given this new-found evidence suggesting these vulnerabilities may have been used in the wild to steal keys, passwords, and e-mail from would-be encrypted Web sessions.Story updated to revise the headline.
reader comments
38