
The cybercrime group controlling the Dyre financial fraud Trojan appears to have suffered a major blow following a Russian law enforcement operation in November. Symantec telemetry has confirmed a virtual cessation of the group’s activities. Dyre (detected by Symantec as Infostealer.Dyre) is spread through email spam campaigns and no Dyre-related spam campaigns have been observed since November 18. Detections of the Dyre Trojan and associated malware have also dropped dramatically since mid-November.
Abrupt cessation of spam campaigns
Dyre is primarily spread through email spam campaigns, most of which masquerade as businesses documents, voicemail, or fax messages. The Dyre group had been running email campaigns on most weekdays, dispatching between one and 15 separate email campaigns per day. However, Dyre-related spam campaigns halted abruptly on November 18 and none have been observed since then, indicating a major disruption in the group’s operations.
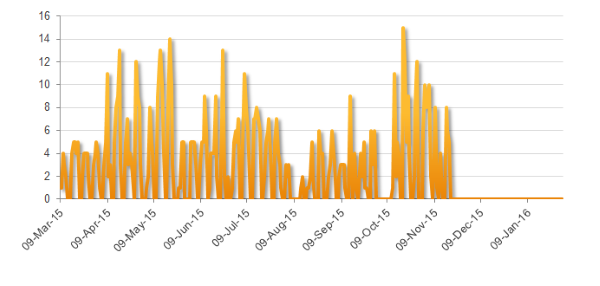
Figure 1. Dyre-related spam campaigns by day from March 2015 onwards. Activity ceases on November 18, 2015.
Dyre spam campaigns come with a malicious attachment, which, if opened, will install the Upatre downloader on their computer (detected by Symantec as Downloader.Upatre).
Upatre collects information about the victim’s computer, attempts to disable security software, and finally downloads and installs the Dyre Trojan. The Dyre group has been one of the main users of Upatre in over the past year. Symantec telemetry indicates a huge fall in the number of Upatre infections since November. The monthly infection rate has fallen below 20,000, after reaching a high of more than 250,000 per month in July 2015.

Figure 2. Upatre infections since January 2015
The number of infections involving the Dyre Trojan itself has also dropped off significantly in the same period. The infection rate was running above 9,000 a month in early 2015. Since November it has fallen to below 600 per month.

Figure 3. Dyre infections since January 2015
Major financial threat
Prior to this takedown, Dyre had emerged as one of the most dangerous financial fraud operations. The Dyre Trojan is configured to defraud the customers of more than 1,000 banks and other companies worldwide. Consumers in English speaking countries, in particular the US and UK were most at risk, since this is where the largest numbers of targeted banks were located.
Dyre targets Windows computers and can defraud victims by snooping on their online banking sessions, stealing their credentials, and sending them back to the attackers. Dyre is also used to infect victims with additional malware and Symantec has to date seen at least seven other malware families being pushed out to infected computers. In many cases, the victim is added to a botnet, which is then used to power further spam campaigns and infect more victims.
Takedowns have no guarantee of success
The move against Dyre appears to be one of the most successful of a number of recent takedown operations against similar financial fraud threats. Unless all of the key figures are arrested and major infrastructure seized, cybercrime groups can quickly rebuild their operations in the aftermath of a law enforcement swoop.
For example, an October 2015 operation against Dridex, one of the other major financial fraud Trojans currently in operation, appears to have had a limited impact on its operations. While one man was charged and thousands of compromised computers were sinkholed, the rate of Dridex infections did not abate following the takedown.

Figure 4. Takedown operation during October 2015 had little impact on Dridex infections
Early indications are that the operation against Dyre has been quite successful, with no sign of the group attempting to re-establish itself. Whether the threat will disappear entirely will become apparent in the coming months.
Protection
- Using an email security solution should remove the chance of accidentally opening malicious email and malicious attachments in the first place.
- Email-filtering services such as Symantec Email Security.cloud can help to filter out potential malicious emails before they can reach users.
- Symantec Messaging Gateway’s Disarm technology can also protect computers from this threat by removing the malicious content from the attached documents before they even reach the user.
Antivirus
Intrusion Prevention System
Further reading
For more information on Dyre, see our whitepaper: Dyre: Emerging threat on financial fraud landscape